The recently discovered ransomware operation known as 'Kasseika' has adopted a technique called Bring Your Own Vulnerable Driver (BYOVD) to incapacitate antivirus software before encrypting files. This tactic involves exploiting a vulnerable driver named Martini (Martini.sys/viragt64.sys), a component of TG Soft's VirtIT Agent System, to disable antivirus products safeguarding the targeted system.
Trend Micro, the cybersecurity firm that uncovered and analyzed Kasseika in December 2023, revealed that this new ransomware strain exhibits numerous attack chains and shares source code similarities with BlackMatter. As BlackMatter's source code has never been publicly leaked since its shutdown in late 2021, it is suggested that Kasseika may have been developed by former members of the threat group or experienced ransomware actors who acquired its code.
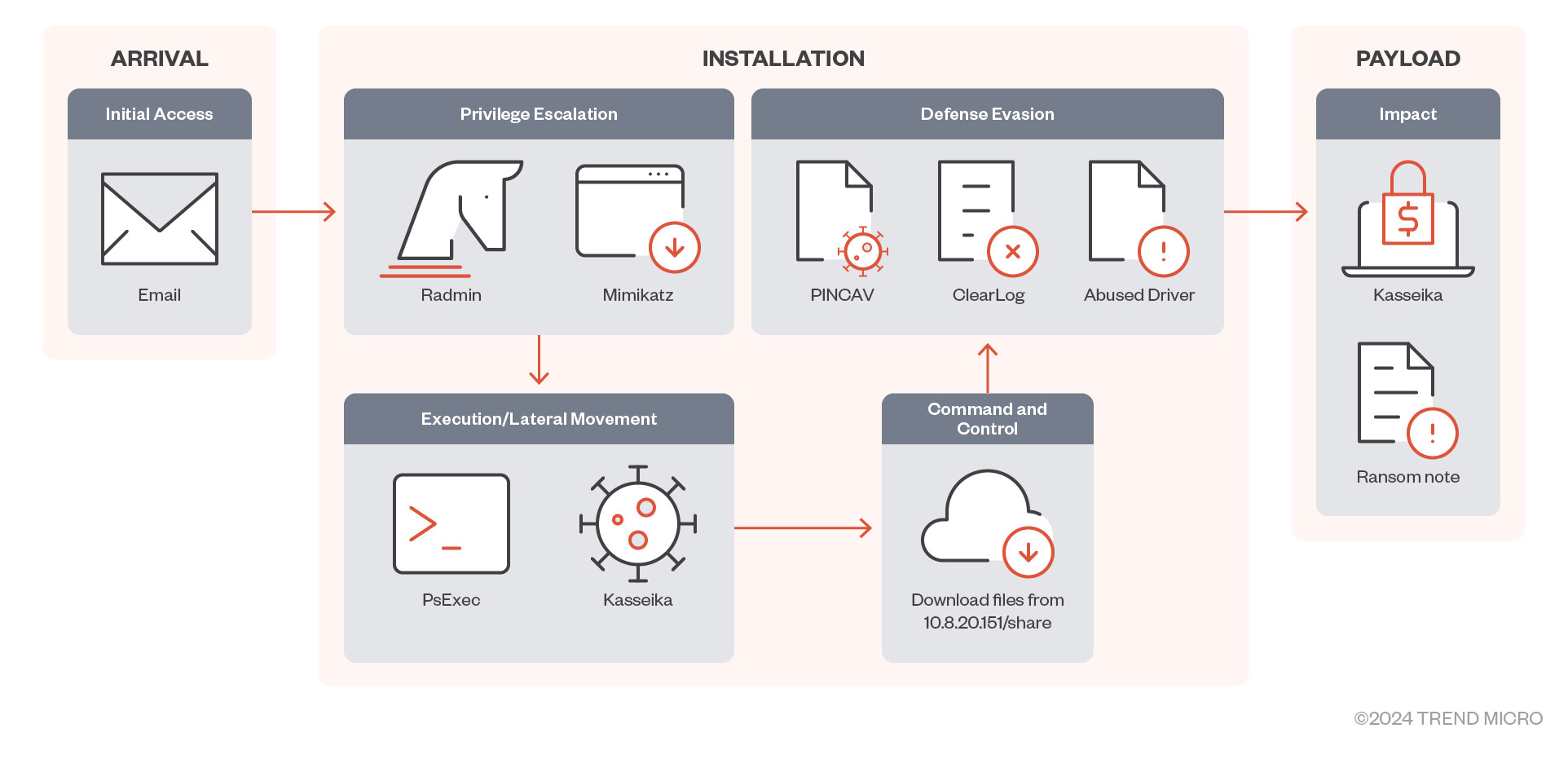
The Kasseika attack chain typically begins with a phishing email sent to employees of the targeted organization, aiming to pilfer their account credentials for initial access to the corporate network. Subsequently, Kasseika operators leverage the Windows PsExec tool to execute malicious .bat files on the infected system and others accessed through lateral movement.
The batch file checks for the presence of a process named 'Martini.exe' and terminates it to avoid interference. It then downloads the vulnerable 'Martini.sys' driver onto the machine. The presence of this driver is critical, as Kasseika will not proceed if the 'Martini' service creation fails or if 'Martini.sys' is not found.
Using BYOVD attacks, the malware gains privileges to terminate 991 processes from a predefined list, including antivirus products, security tools, analysis tools, and system utilities. Kasseika subsequently executes Martini.exe to terminate antivirus processes and launches the primary ransomware binary (smartscreen_protected.exe). Afterward, it runs a 'clear.bat' script to eliminate traces of the attack.
Kasseika employs the ChaCha20 and RSA encryption algorithms to encrypt target files, appending a pseudo-random string to filenames, a technique reminiscent of BlackMatter. The ransomware drops a ransom note in every encrypted directory and alters the computer's wallpaper to display information about the attack.
To further obscure its activities, Kasseika clears system event logs post-encryption using commands like 'wevutil.exe.' In observed attacks, victims were given 72 hours to deposit 50 Bitcoins ($2,000,000), with an additional $500,000 added for every 24 hours of delay. To receive a decrypter, victims are instructed to post a screenshot of payment proof on a private Telegram group within a maximum deadline of 120 hours (5 days).
Trend Micro has released indicators of compromise (IoCs) related to the Kasseika threat for identification and mitigation purposes.
Source: TrendMicro




0 comments:
Post a Comment